
The Problem With Consumer Data Today
Today, more than ever, Muslims and those of other faiths have embraced the digital world to become an integral part of who they are and what their lives look like. For more than two decades consumers have been leaving digital footprints that have dehumanized them by turning them into commodities.
The lack of explicit consent to the use of their data is not only questionable ethically but also from an Islamic perspective for advertising. This is why Muslim brands should jump at the opportunity of implementing the protection of consumer privacy with the ever-increasing compliance rules and regulations in combination with the ever-improving privacy enhancement tools.
The rush to make a buck from massive data use has led to data breaches and misuse of consumer data that is on the borderline of crime. This has brought about a turnaround by the giants of tech, with Apple taking serious measures to cut down on user tracking and Google retiring third-party cookies in 2024.
Read: “Advertising to Muslims Online in 2024 After Third-Party Cookies Disappear”
One of the most important things your halal business must understand about where advertising is heading, what data will look like, and what that means to your efforts in advertising to Muslims. The most basic part for your Muslim brand to learn about is identity resolution which we covered in our article, “Halal Advertising Must Get Serious About ID Resolution”. In a nutshell:
“Identity resolution – the science of connecting the growing volume of consumer identifiers to one individual as he or she interacts across channels and devices – has become critical to marketing success, as well as essential for compliance with consumer privacy laws such as the California Consumer Privacy Act (CCPA) and the European Union’s General Data Protection Regulation (GDPR).” – MarTech
Introducing Privacy Enhancing Technologies
The other critical component of the consumer privacy revolution is the rapid rise of tools that have been created for advertisers to do what they need to do without violating the privacy of consumers. These are known as Privacy Enhancing Technologies, abbreviated as PETs.
Privacy Enhancing Technologies (PETs) are important tools that help protect consumer personal information. These technologies work by using only necessary consumer data, making the data more secure, and giving consumers more control over their personal information. Overall, PETs help uphold consumer privacy rights in the digital world.
What PETs Have to Offer Your Muslim Brand
As mentioned, PETs are designed to collect only the necessary information and not more. This can be compared to only taking what you need and not overloading your database with extra stuff. By doing this, your halal brand avoids having too much information which, from an ethical perspective, helps prevent problems like data breaches or unauthorized access.
Read: “The Ultimate Lesson From the Muslim Pro User Data Scandal”
But also from an Islamic perspective helps you to adhere to the rule of avoiding Israaf (extravagance). As Raaghib Isfehaani – an eleventh-century Muslim scholar of Qur’anic exegesis and the Arabic language – put it, “Any action which an individual performs which exceeds the limits is considered as being Israaf”.
PETs also ensure that your consumers’ data is optimally safe. They make use of advanced encryption methodologies, authentication protocols, and stringent access controls, forming formidable barriers that discourage unauthorized intrusions. Even if someone manages to break in, the information they steal is like a puzzle without a solution. This type of data security is indispensable in preventing breaches that could lead to privacy violations and instances of identity theft.
PETs will empower your targeted Muslim audience by affording them greater control over their personal data. In today’s digital landscape, consumers often encounter situations where their data is collected and utilized without their explicit consent goes against the concept of mutual goodwill.
”O you who believe! Eat not up your property among yourselves in vanities: But let there be amongst you traffic and trade by mutual goodwill.” [ Quran 4:29]
Privacy Enhancing Technologies disrupt this pattern by introducing features such as data anonymization and pseudonymization. These mechanisms allow individuals to share data while retaining their anonymity, preserving their sense of privacy while still enabling valuable data-driven services.
Moreover, PETs provide a platform for innovative concepts like data trusts or vaults, which enable consumers to maintain ownership of their data while permitting controlled access to specific sections of that data. This model fosters a collaborative environment where your Muslim audience can share data for research or other purposes, all without compromising their personal privacy. This creates harmony between data utility and personal autonomy and reshapes the way data is managed and shared.
The Challenge of Implementing PETs
However, there is no solution without a blemish. Seamless integration of PETs comes with its own set of challenges. The implementation of PETs like every new phenomenon requires specialized expertise. This can potentially exacerbate the divide between those well-versed in these technologies and those who are not. Balancing the scales between privacy preservation and data utility is also no easy task, as an overemphasis on privacy could potentially stifle innovation and the development of beneficial services.
Also, navigating the evolving terrain of privacy regulations adds complexity to the adoption of PETs. Different regions adhere to distinct data protection regulations, requiring adaptable approaches to implementation. Collaborative efforts among technologists, policymakers, and legal experts are crucial to ensure that PETs align with global privacy standards while remaining sensitive to local complexities.
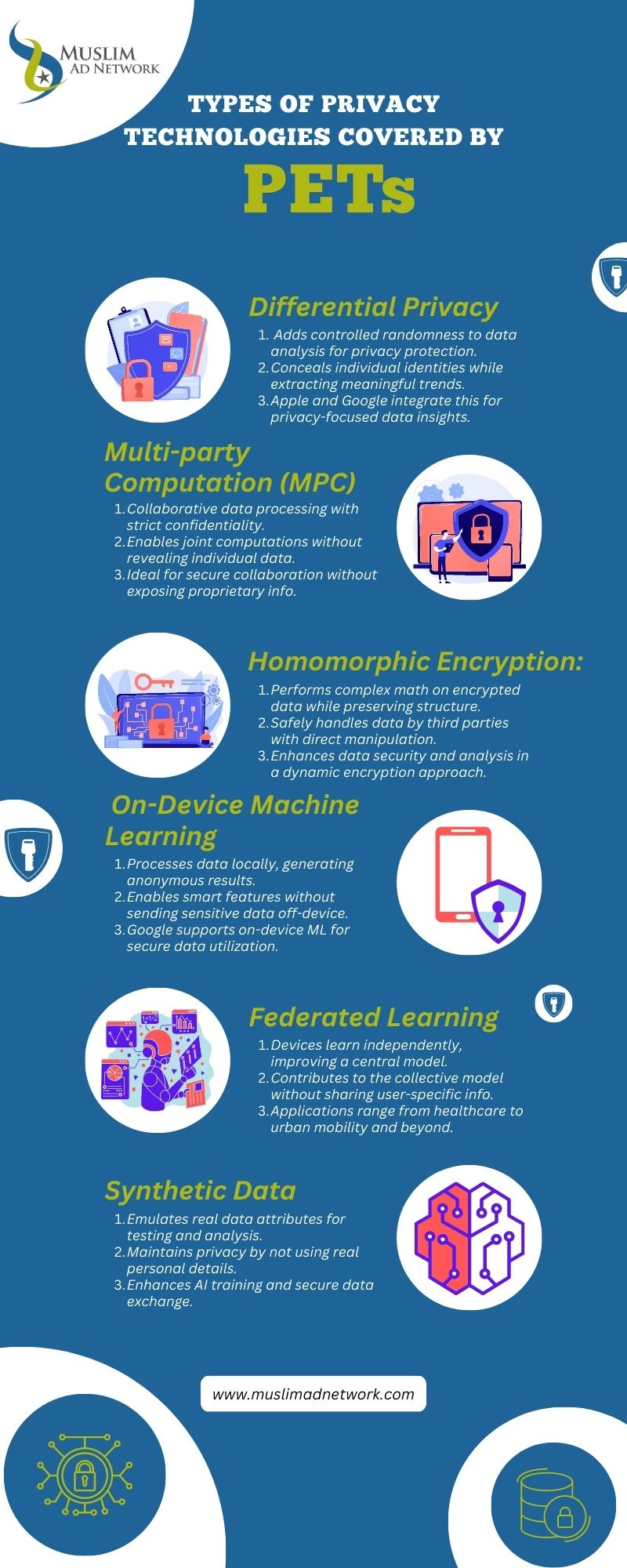
Differential Privacy
Differential Privacy is a groundbreaking approach that addresses the dual challenge of data analysis and individual privacy protection. By adding controlled randomness to data before analysis, it ensures that specific individuals cannot be distinguished within the dataset, enabling the extraction of meaningful trends while preserving privacy.
Imagine attending an event where everyone wears the same attire, making it impossible to identify individuals. This notion resembles how Differential Privacy operates, it will obscure your Muslim audience’s data of individuals by introducing calculated noise. This prevents unauthorized identification while allowing accurate analysis of collective patterns.
Differential Privacy stands as a crucial advancement compared to traditional data anonymization, which can still lead to privacy breaches through data linkage. Notably, industry giants like Apple and Google have integrated these principles. Apple’s SkAdNetwork lets advertisers gauge ad campaign success without accessing personal data. Google’s Privacy Sandbox aims to reshape targeted advertising while prioritizing privacy. We will delve into both a bit later in this article.
Multi-party Computation
Multi-party Computation (MPC) is a cryptographic method designed to facilitate collaborative data processing among multiple participants while maintaining strict data confidentiality. Think of it as a solution that allows your Muslim brand to access data analysis from various parties that contribute insights and information to a shared project without exposing their individual source materials. This concept finds practical application in initiatives where companies seek to collaborate without compromising their proprietary information.
At its core, MPC operates by enabling multiple parties to jointly execute computations on data without gaining access to any details beyond their own contributed input and the resulting output of these computations. This means that each participant’s data input remains concealed from the others, ensuring a high level of privacy. To accomplish this, the data is first encrypted through a process that involves splitting it into “secret-shares” using random partitioning. Remarkably, these secret-shares possess the property of not revealing any discernible information about the original data on their own. These confidential secret-shares are then allocated across multiple servers.
Homomorphic Encryption
Homomorphic encryption offers a novel approach to data security. It involves converting data into an encrypted form, allowing complex mathematical operations to be performed on it without compromising the encryption. This concept preserves the original data’s structure, enabling consistent results whether computations are done on encrypted or decrypted data.
Unlike traditional methods, homomorphic encryption permits direct mathematical manipulation of encrypted data, making it safer when handled by third parties. It supports secure data analysis, sharing, and processing. Despite its potential, challenges such as performance limitations exist.
Implementing homomorphic encryption requires careful consideration of data needs and risks. Regular evaluation and updates of solutions are essential. This innovation showcases the dynamic nature of encryption techniques, providing a robust tool for heightened data protection in today’s digital landscape.
On-Device Machine Learning
This concept is comparable to storing valuable possessions in a secure vault at your premises. With on-device learning, your data remains confined to your device. Specific calculations are performed onsite, generating only broad, anonymous results devoid of any sensitive content.
According to Google:
- By using on-device ML, the data processing can happen on your user’s device. This means that you can also apply machine learning to sensitive data which you would not want to leave the device.
- If you apply end-to-end encryption for data — like messages — on-device machine learning still makes it possible to provide smart data-powered features.
Source: “Why On-Device Machine Learning?”
Federated Learning
Staying on devices, through federated learning, devices independently learn and adjust, while the general knowledge they acquire is combined to improve a central model ( the master project file for a work-shared project) without involving specific user information.
A multitude of connected devices, including phones, watches, vehicles, cameras, and more, equipped with sensors and computational power, can contribute to training models collectively. In our everyday world, federated learning extends its utility to different organizations, allowing hospitals and pharmaceutical companies to enhance treatments and drug development without compromising sensitive data.
This framework’s potential extends to complex systems like urban mobility, economic markets, energy usage, climate change, and public health. Ultimately, federated learning can foster collaboration in data analysis while preserving data ownership for individuals, companies, and institutions.
Synthetic Data
Imagine it as a surrogate or duplicate for authentic data. Although not genuine, it closely emulates key attributes of real sets of data, making it practically usable. It operates as a copy that mirrors the fundamental framework without involving any real personal particulars. This technique proves invaluable for testing and analysis purposes, all the while maintaining the exclusion of actual user data.
Synthetic data transcends the realm of simulated information and surpasses authentic data. It serves as an adaptable material for AI training. It also facilitates secure customer data exchange both within and beyond organizational boundaries.
A central advantage of synthetic data generation is its superior approach to data anonymization. In contrast to modifying and thereby compromising an existing dataset, synthetic data originates from scratch. This is achieved while retaining the correlations and patterns present in the original training data for the synthetic data generator.
Initially, a smart computer system learns all the details and patterns in the real dataset. Then, it uses this knowledge to create new substitute data that looks just like the original. This substitute data is very similar to the original and keeps identities hidden, so there’s no way to connect it back to real people. This ensures that the risk of identifying someone from the data is eliminated.
Privacy Enhancing Technologies Your Muslim Business Should Know About
Here are a few remarkable instances of privacy technology applications, frequently incorporating one or more elements that we previously examined:
Apple’s SkAdNetwork and App Tracking Transparency Framework
These tools exemplify Apple’s recent commitment to user privacy. SkAdNetwork facilitates campaign attribution while safeguarding user identity, and the App Tracking Transparency framework empowers users with the option to control their tracking preferences across third-party apps and websites.
Preserved User Privacy: SKAdNetwork measures conversion rates without compromising user identities. This is essential for Muslim brands aiming to build trust and maintain a positive image by prioritizing user privacy.
Enhanced User Trust: Muslim advertisers striving to maintain a positive brand reputation and user trust will find SKAdNetwork’s privacy safeguards advantageous.
While SKAdNetwork offers great privacy benefits, it also presents some privacy challenges for Muslim brands:
Fraud Vulnerability: Unencrypted post-install conversion data in SKAdNetwork can be manipulated by fraudsters.
Distributed Data: Data distribution across multiple networks can complicate data management for Muslim brands using multiple ad networks.
To overcome these challenges, Muslim brands should tailor strategies to their unique objectives, ensuring efficient use of SKAdNetwork while mitigating potential issues.
Google’s Privacy Sandbox for Web and Android
Google’s Privacy Sandbox for Web and Android is a child of its aim to set privacy-focused benchmarks for the internet. Its goal is to equip publishers, advertisers, and developers with the necessary tools for online business activities, all the while upholding user privacy considerations.
It is also Google’s attempt to forgo classic cookie tracking on the web. The Privacy Sandbox itself has been around for quite a while. If you were around when SEO first started becoming a thing, the name will be familiar to you.
“The idea of Google sandbox dates back at least 15 years… The sandbox is believed to be a filter for new websites. The assumption is that the filter traps new sites and doesn’t let them rank until they reach a certain age.” – SEO PowerSuite
The Privacy Sandbox bridges the gap between successfully defending customer privacy and giving your Muslim organization the data and tools it needs to continue to target its ads in positive ways.
Other Privacy Technology Applications
Meta’s Conversions API: Meta has been in hot water due to privacy issues for a while now. Due to increasing privacy restrictions, the Meta Conversions API was created to enable you as an advertiser to stream web events directly from your servers to Facebook. Usually, it would first be sent to the browser responsible for sending an event. With Conversion API you can process data as a first-party cookie to avoid conversion loss due to browser cookie restrictions.
Data Clean Rooms: Data Clean Rooms serve aggregated and anonymous customer information. As an advertiser, you will access non-personally identifiable information (non-PII) to target a specific demographic and audience measurement. For example, if you extract specific data sets that show people who increase the purchase of gifts during Eid or Ramadan, you could be looking at a goldmine without having to know who those people are. This could be why, particularly in the retail media, clean data classrooms continue to gain popularity, as they facilitate knowledge bartering without revealing proprietary information. We talk more about Data Clean Rooms in our article: “Halal Advertising Must Get Serious About ID Resolution”.
These technologies are not the finished item yet. However, as adjustments and improvements are made, it is clear that they have the potential to balance consumer stewardship with the data needs of digital marketers.
With that said, here is what your Muslim business should expect in the coming years:
- The new, increasingly digitally savvy halal customer will want more of a say over their data.
- Your halal brand will have to leverage real-time polls, interactive content, and community forums, to collect information directly from your Muslim audiences.
- Halal brands will increasingly depend on partnerships with platforms that specialize in serving ads to Muslims.
Conclusion
As privacy regulations continue to evolve, organizations are increasingly finding that they are turning to Privacy Enhancing Technologies to protect personal data. As outlined in this article, there are many different types of PETs, each designed to solve a specific business problem. Some are better for deriving insights from sensitive data while others are best for data exploration. Regardless, they will be a valuable part of your halal brand’s privacy toolkit, and, knowing that you have dealt with and tackled privacy risks that might come your way, can give you increasing confidence.
PETs will bring about change in the way advertising works, that’s a given, but rather than back away from the inevitable, now is the time to lean in and educate yourself and the team behind your halal brand.
You may be doing great work, and nobody wants to hinder innovation, but we need to be able to balance great ideas and innovation with respect for people and their data. This is essential for your business’s public perception and future.
start targeting muslim consumers